Since the preview release of shell script support for macs in Microsoft Endpoint Manager the platform is becoming increasingly more competent to manage more complex macOS scenarios in an enterprise. Microsoft also states that for simpler management MEM is ready for enterprise. If you on the other hand have more complex management scenarios such as:
- Complex application deployment
- More complex script deployment and actions
- Custom PLIST
- IFTT
- Complex printer deploy
You will need to run MEM and Jamf togheter. Let’s face it, you cannot achive a better Apple management than you can with Jamf who has been leading iOS and macOS management for years.
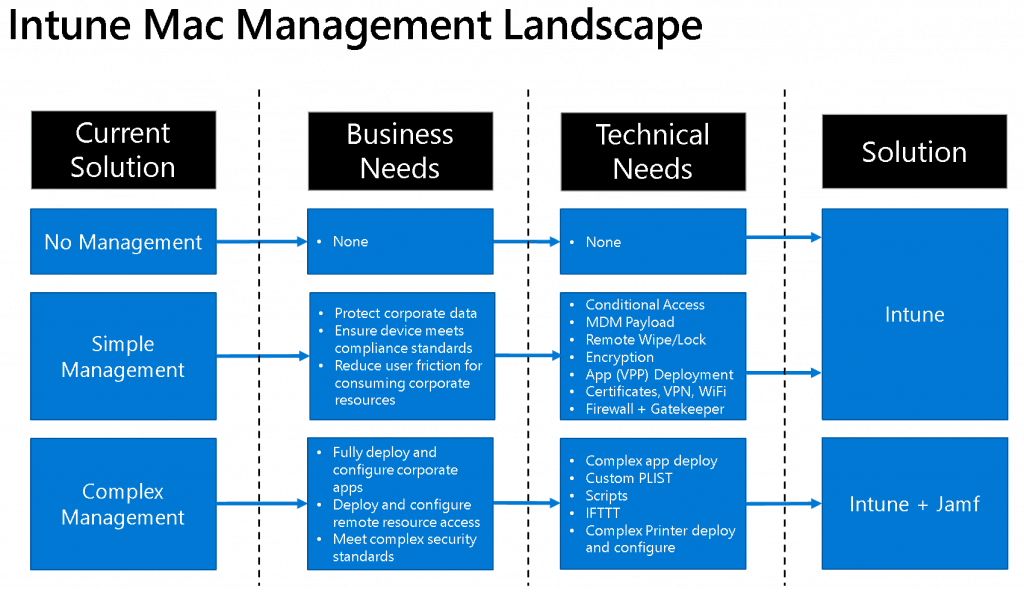
This is what Microsoft said about the Mac management landscape at Ignite 2019
The beauty in all this is Microsoft’s partnership with Jamf which means that we can get the best management available while also being able to use conditional access policies on Azure based on compliance. This is a really powerful tool.
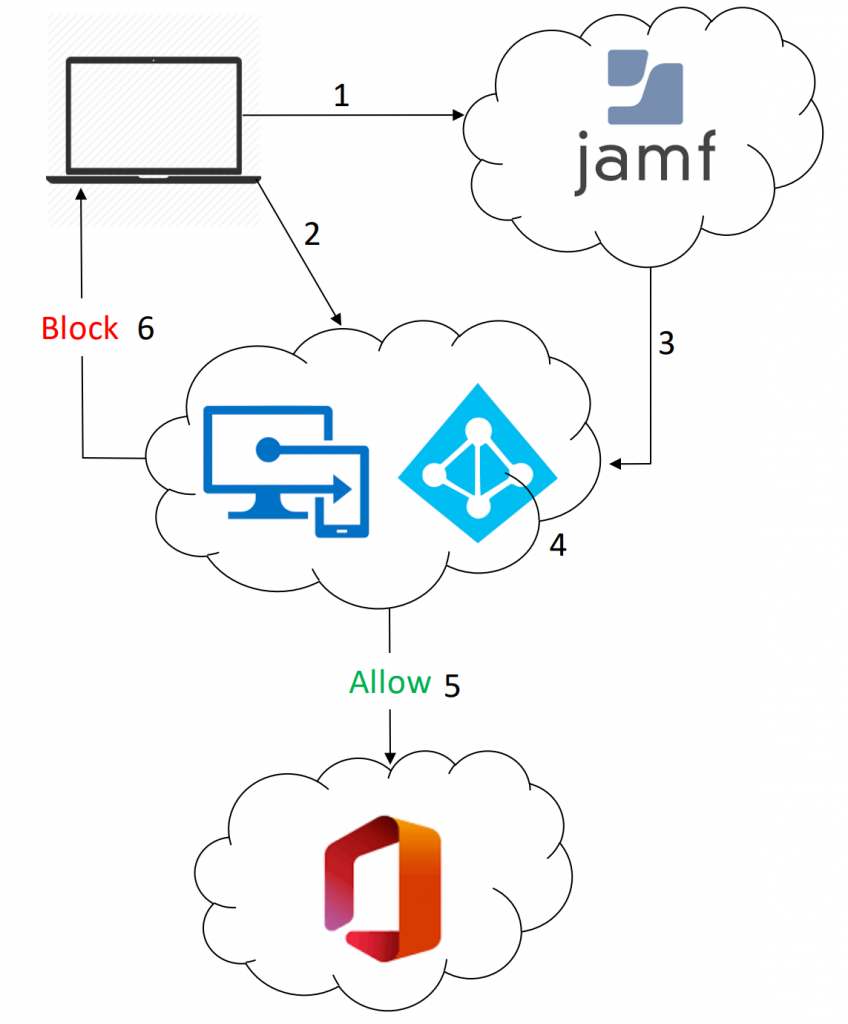
1. Mac is managed by Jamf Pro
2. Mac is registered with Microsoft Intune
3. Jamf sends macOS device inventory to Microsoft Intune
4. Microsoft Intune evaluates compliance, generates a report, and enforces conditional access via Azure AD
5. Allow access from compliant devices
6. Block access from noncompliant devices, and provide a user-friendly remediation experience powered by Microsoft Intune and Jamf
Let’s get started with integration
First, let’s have a look at some prerequisites.
- Jamf Pro 10.1.0 or later
- Company Portal app for macOS
- macOS devices with OS X 10.12 Yosemite or later
We’re going to make the integration in three steps
- Register a new app in Azure
- Enable integration in MEM
- Configure Jamf for integration
1. Register app in Azure
- login to the azure portal and then open Azure Active Directory -> App Registrations, select new registration.
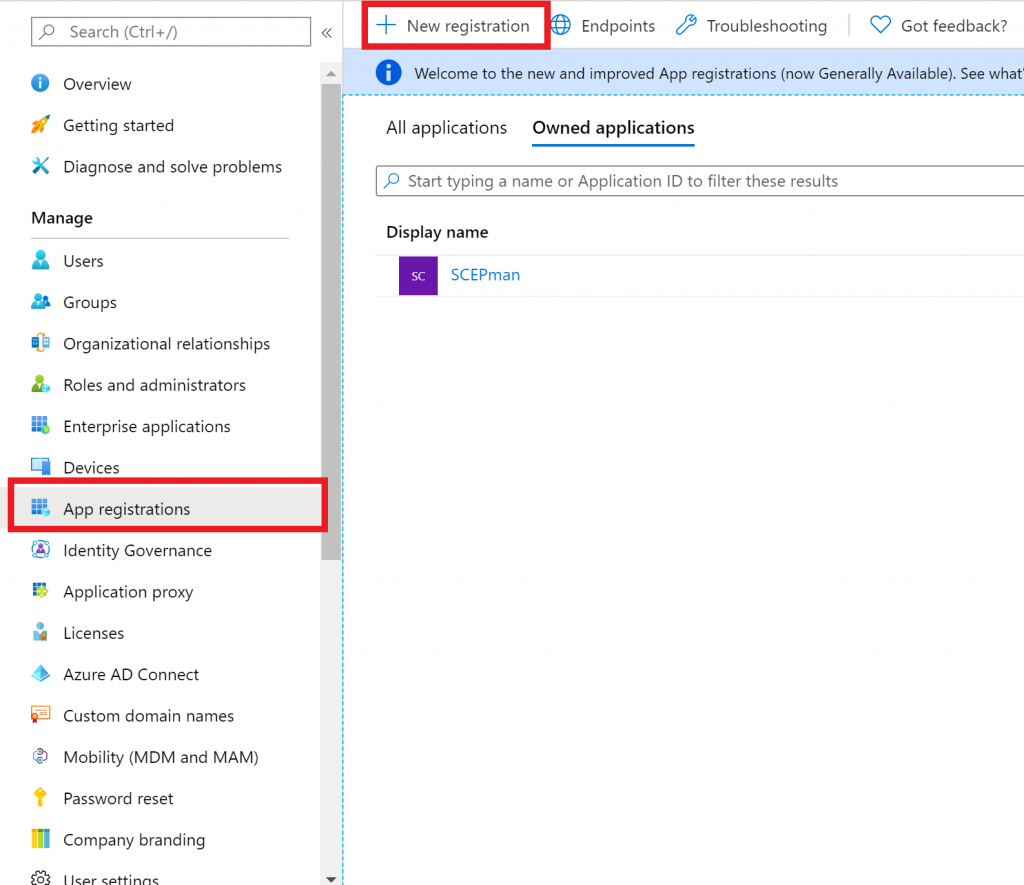
- Give the app a name, for example Jamf Pro CA, choose Accounts in any organizational directory and then click on Register.
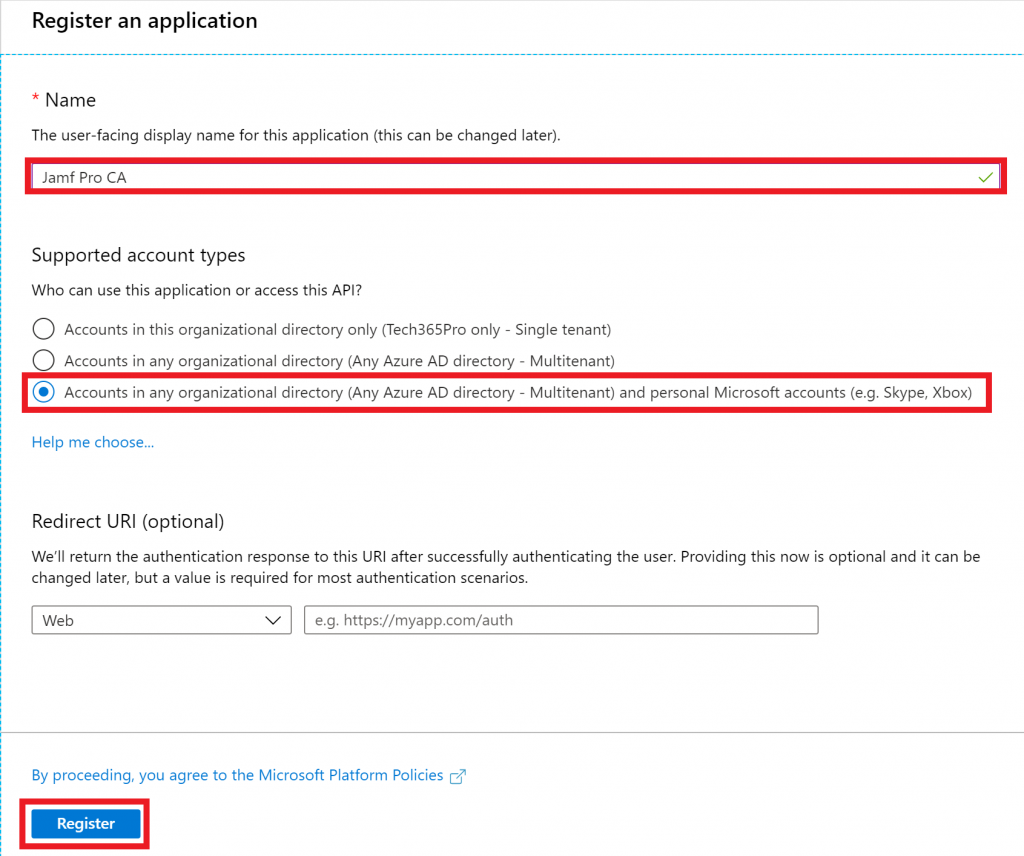
On the overview page, copy the Application (client) ID. We’ll need this later.
- Go to Certificates & secrets and click on New client secret, give it a Description, select any Expires option then click on Add. Be sure to copy the Value from the client secret before you leave the page, we’ll need this later.
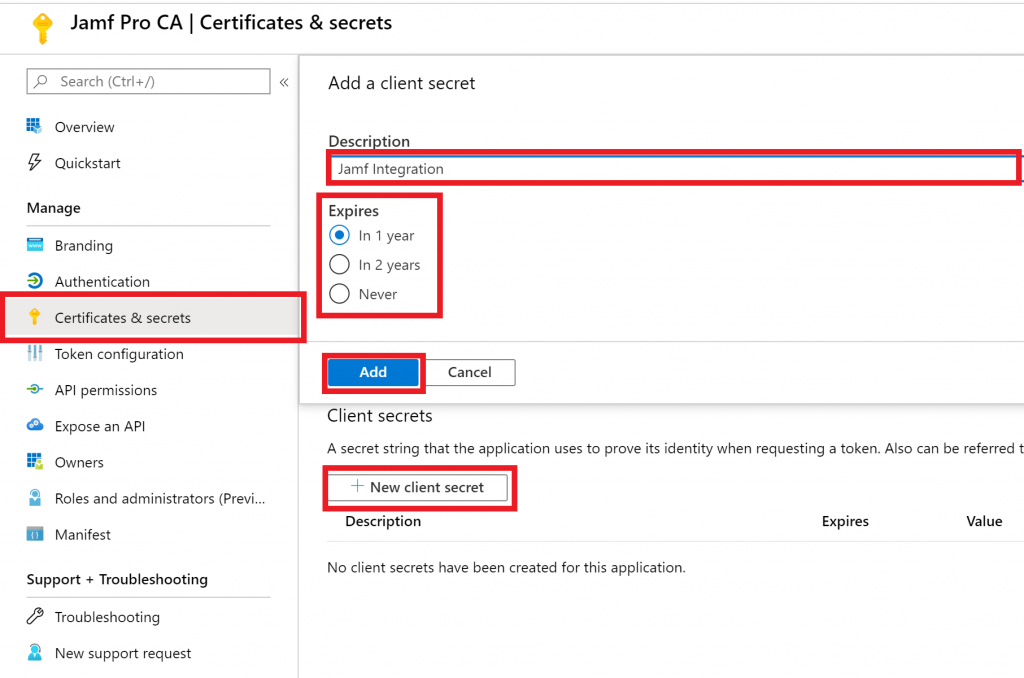
- Next, click on API permissions -> Add a permission and select Intune and then Application permissions.
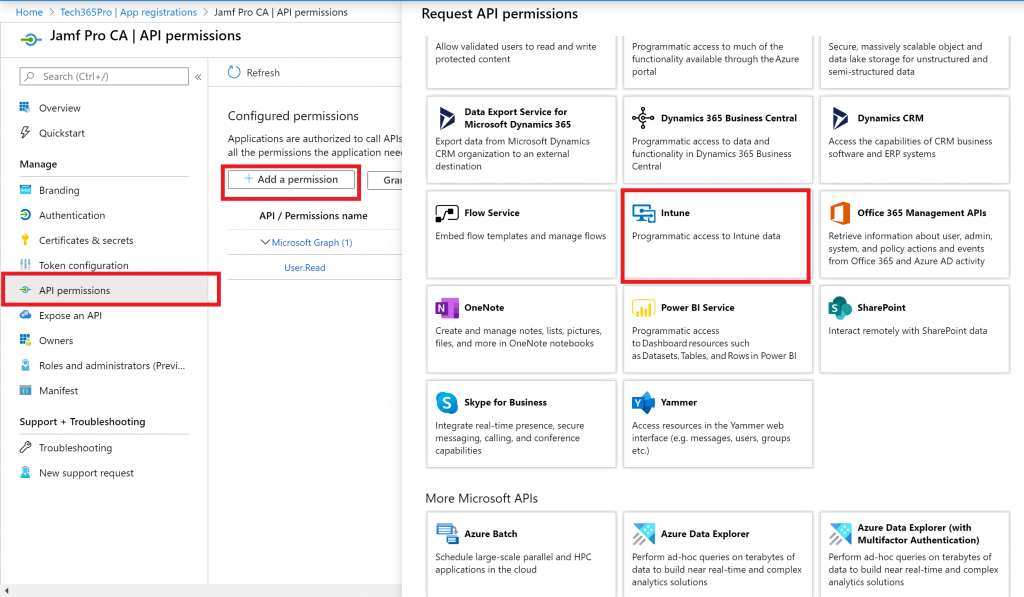
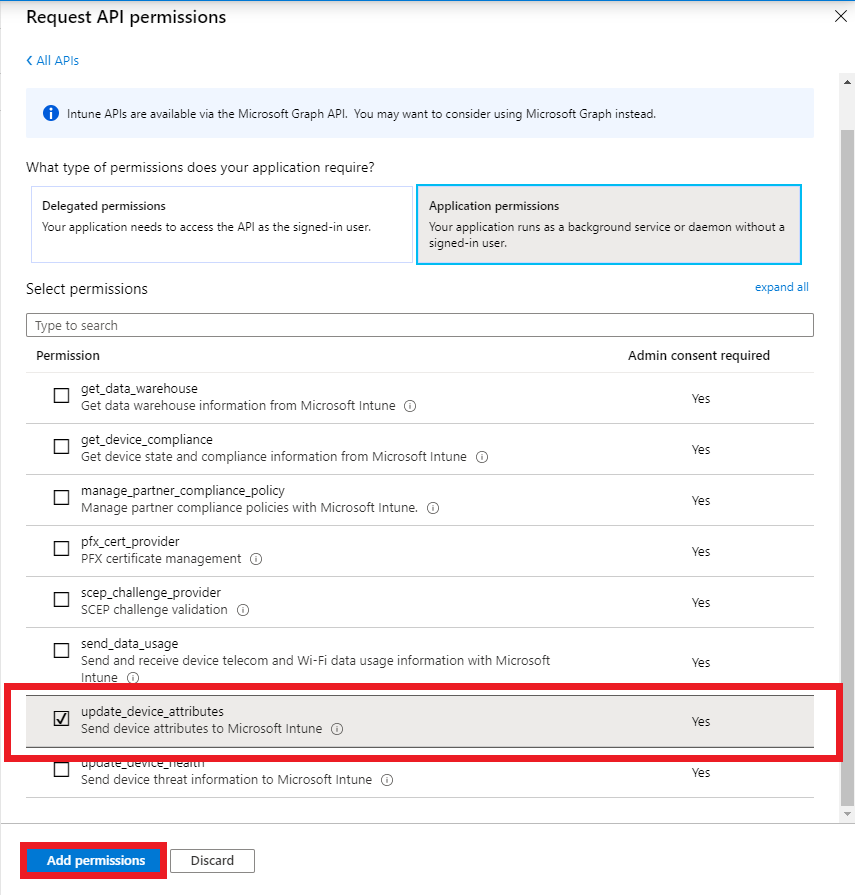
- Select update_device_attributes and then click on Add permissions.
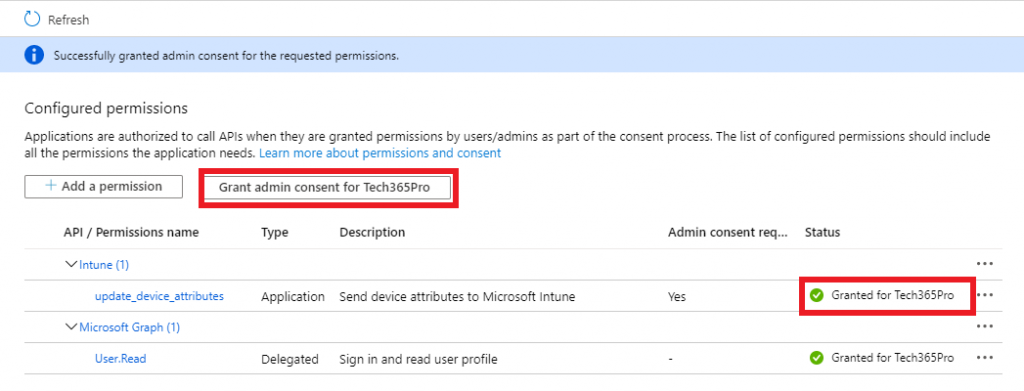
- Click on Grand admin consent for [your tenant] and make sure status changes to Granted for [your tenant]. After this, the app registration is complete.
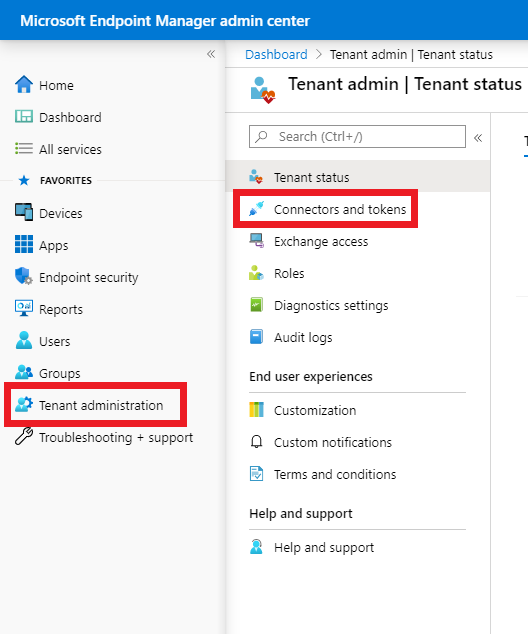
2. Enable integration in Microsoft Endpoint Manager
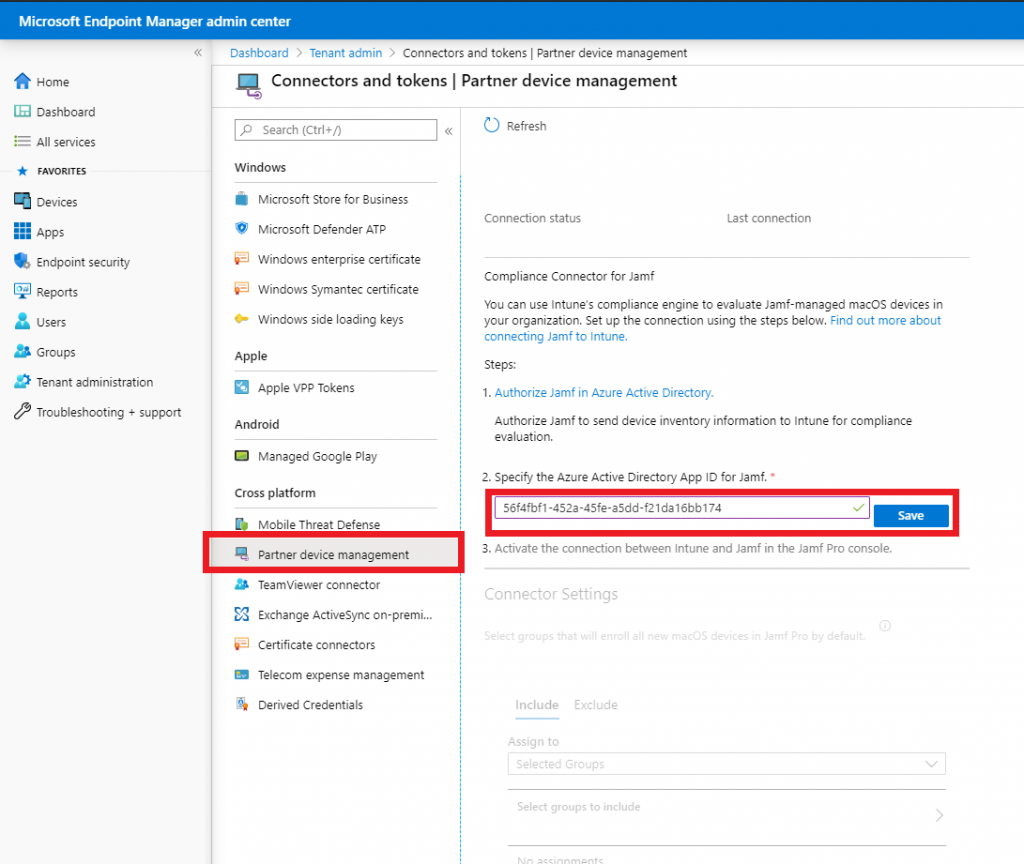
- Sign in to the MEM console, then click on Tenant administration -> Connectors and tokens.
- Choose Partner device management and activate the integration by pasting the Application (client) ID you copied earlier, then click Save.
3. Configure Jamf for integration
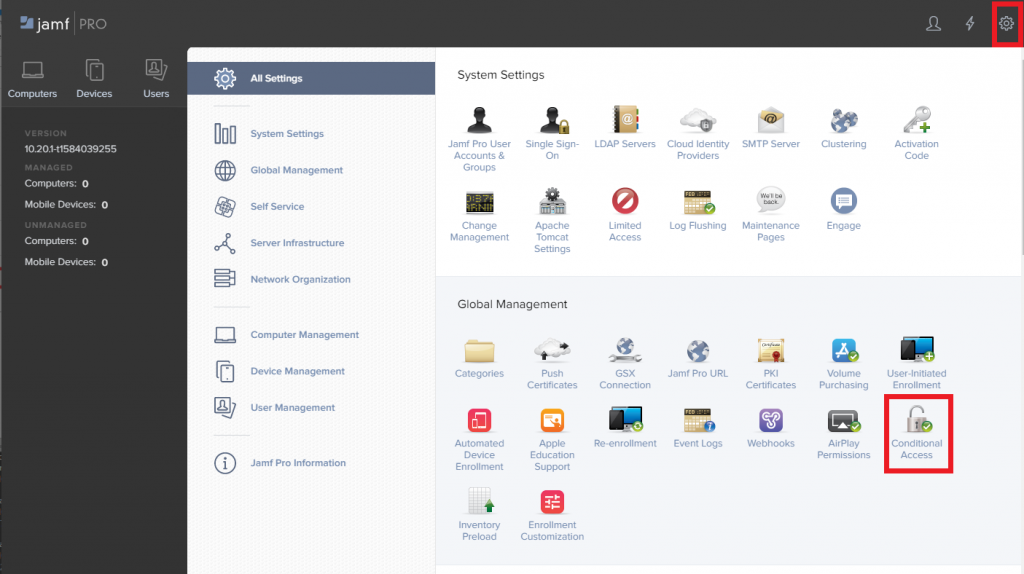
- Sign in to your Jamf Pro console, then click on Settings and under Global management, select Conditional access.
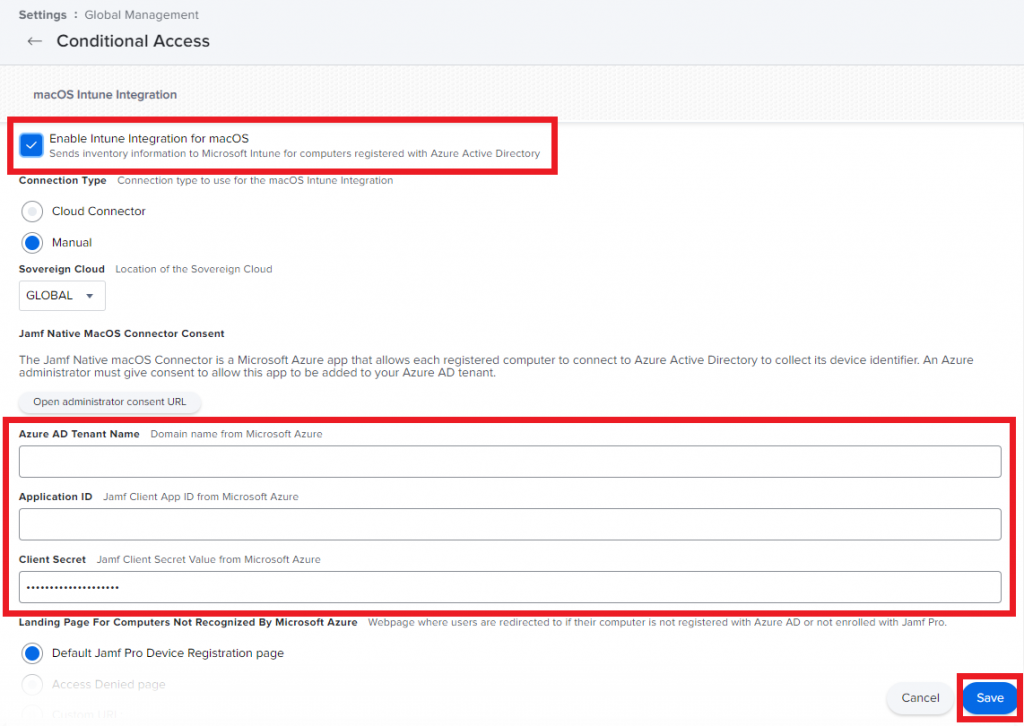
- Check the Enable Intune Integration for macOS box. For Azure AD Tenant Name, enter your Azure AD Directory ID which you can find in Azure AD -> Properties. I know it says Tenant name but the ID is what is required, at least in my testing. Then continue to enter your Application (client) ID and Client Secret that you copied earlier, then click on Save.
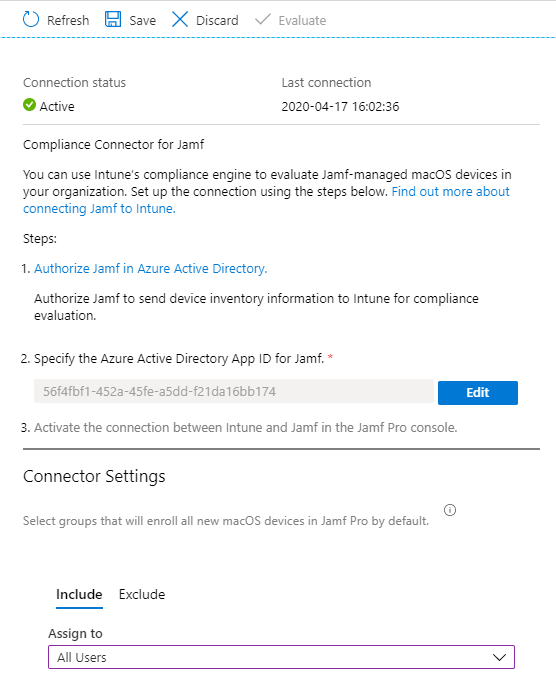
- Go back to the Partner device management page in MEM console, the connection is now active. If you want all users to enroll with Jamf by default leave Assign to the default All users value. Otherwise you can select specific users by adding your group.
Next you will need to deploy Company Portal to devices using Jamf and setup compliance policies for macs managed by Jamf.
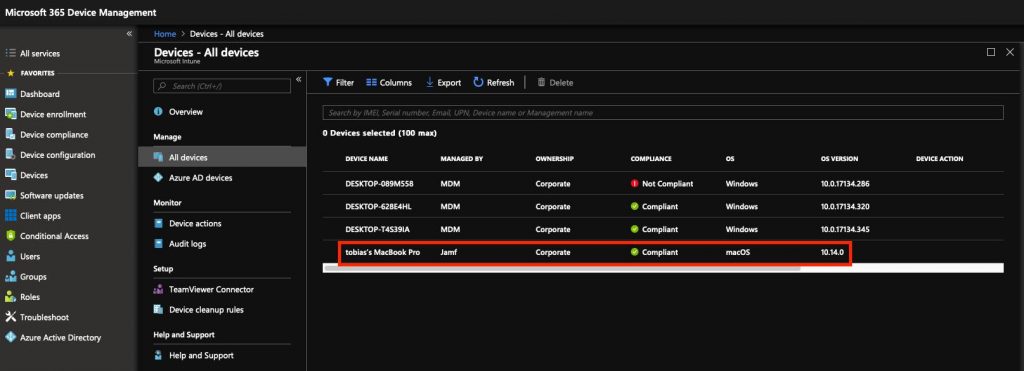
Devices that are managed by Jamf will now start showing up in MEM as compliant devices and you can start using Conditional Access on them. Pretty cool if you ask me 😊.